CyberSecurity was the topic of CORE’s first Lunch ‘n’ Learn Event of 2018, held on the Second Thursday of February at The Point Pub & Grill in Central Point.

Scott Anderson, CEO of CORE Business Services, teamed-up with Tom Kaldunski, Agent at Hart Insurance to educate users on CyberSecurity and the need for Cyber Insurance.

Desperados of Yesteryear
Tom launched the seminar by reminding the audience about the escapades of desperados Bonnie & Clyde, the infamous Depression Era bank robbers, back in the 1930s. The Why was simple: that’s where the money was.
Current Day Desperados
Who are the current day desperados? Tech-educated people. They are after something way more valuable and easier to access than the bank’s money: information. And, since we all traffic in information, the size of the market is huge.
Tom then turned over the presentation to Scott, who manages a team of people whose purpose in life is to combat the modern-day desperados.

Threat Landscape
Scott began by asking, “What’s today’s Threat Landscape? What are we up against? We know cyber is this huge word—and security is the biggest word. But before we continue, we first have to be clear about the composition of the Web.”

Image Link: <http://www.cyberinject.com/difference-deep-web-darknet-dark-web/>
Surface Web
Scott sees the Web as a place to check his sports scores at the end of the day. If you take a closer look at the image above, the Surface Web is where the majority of us spend our time; general information searches (like sports scores) are conducted in the space that consumes about 4% of the Web.
Deep Web
The Deep Web consumes about 90% of the Web. That includes password-protected information controlled and managed by government sites, healthcare sites and record-keeping sites that aren’t crawlable or searchable via Google or other search engines; this segment makes up more of the private Web.
Dark Web
The deeper portion, the Dark Web, makes up 6% of the Web. Most of us spend the majority of our time in the 4% of the Surface Web but there’s more to the Dark Web than there is to the Surface Web.
With that clarification of the Web, Scott moved on to motivation.
The Value of Information
We are all aware of the fact that our financial information can get hacked. So what are those Dark Web Guys going to steal, and what are they getting for that information on the dark—or black—market?
Scott continued his presentation by displaying a slide entitled, What Is Your Information Worth? with a list of the incentives for misbehavior:
- Social Security Number: $1.00
- Credit Card Number with CCV on the back of the card: $5.00
- Credit Card Number that includes digital Bank Info: $15.00
- Credit Card with Fullz Info: $30.00
- Pay Pal or other online financial accounts: $20.00 – $200.00
Phishing
How are people getting this personal financial information?
Phishing is the biggest method in use today. CORE does a lot of Phish Campaign Testing with clients where CORE actually becomes a Phisherman, sends out a fake phishing email to their clients, and then reports back to the client on the success of the campaign. These results become something the client company can use to either pat people on the back—or initiate educational or disciplinary action.
Phishing Example
Company X has 265 users in their company, and uses Office 365 as the email vehicle. 160 users opened CORE’s test email. About 42 of them (18% of users) clicked the link in the email. And, about 10% of the users actually entered their Office 365 credentials in the link. Keep in mind that, for most people, our email password is the same as our banking and other passwords.
Phishing Attacks
91% of breaches start with a phishing attack.
While there are many tactics we can use to prevent attacks, a lot of prevention comes down to our users, and what we are doing on a training and awareness level. As a point of interest, Scott cited a scary statistic about phishing attacks: 26% of the successful ones involve someone clicking on the attachments to invoices.
Phishing prevention comes down to awareness—employee awareness, from the base all the way up to the top of the company org chart.
Spam is Morphing
For the past couple of years (starting in early 2016), the number of spam attacks has remained at about the same level but spam attacks with malicious attachments have skyrocketed. The analysis is: spam has become so ubiquitous and accepted that spammers figure why not add some malicious payloads to the spam? The takeaway? Spam used to be an inconvenience; now it’s a pretty big security risk.
Spam Statistics
- One in a hundred emails contains malware.
- Phishing attacks caused $3.1 billion in losses in 2016.
- 30% of phishing messages are opened.
- Phishing emails have six times the click-through rate of genuine marketing emails.
These attacks are happening so often that statistically, the phishers will probably succeed more often than not. The Dark Web is big business. These are not simply hackers; these are top-notch Web marketers.
Spoof Example
Scott displayed an excellent example of spoofing the Wells Fargo Bank website. The image showed an example of a web page that exactly replicated an actual Wells Fargo web page, with one small exception: the Account Login Link probably resolves to the Phisherman’s site where the Phisherman captures all the user’s account information.
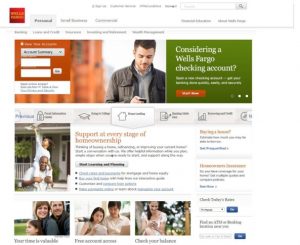
Replica of Spoof Wells Fargo Website from CORE presentation.
Malware Operation
Most malware is not executed by simply opening an email. The act of clicking on the link inside the email is what triggers the malware; that’s either going to launch the malware or take you to a site that requests credentials.
Third-party software that can’t be automatically updated is where the majority of issues occur. Common examples include programs like Chrome, Java, Adobe.
Malware Example
The example below is telling you to update something.
***Email Replica***
! This message is high-priority.
Action Items
From: Mail Deliver System [mailto:joebarnes@someconstructioncompany.com]
Sent: Tuesday, September 19, 2017 2:57 PM
To: Joe Barnes <Joe@anothercompany.com>
Subject: Your new Office mail configuration settings
Dear Client,
Your storage space for Office account: Joe@anothercompany.com is almost full.
92% Used
You need to retrieve pending incoming emails and save your new configuration settings.
Click http://quota.microsoftonline.com/ to add additional 10 gig free and mandatory storage.
Regards,
Mail sent to: Joe@anothercompany.com
***End Email Replica***
The email is from someone you know (who probably got hacked at some point), and you open the email and click on the document link. A lot of these types of emails come from bad patches. Bottom Line: Don’t click something that doesn’t sound legitimate; you could be enabling a macro that will download malware.
Meet The Malware Market
Why is malware growing so much? Because malware is so easy to create. There are actually websites (e.g., OffensiveWare; a malware-as-a-service platform) that offer to sell [to hackers] one exploit for $49—or an unlimited number for $290. And, these places have their own online Tech Support Teams! They have step-by-step Exploit Builders on their website, which is conceptually-equivalent to a user-friendly IDE (similar to commonly-used app builder software.) They also provide a Hosting Button that lets you host your malware on one of their subdomains until you have had a chance to build your own website.
Data-Stealing Malware
Malware acts by entering your system—and then stealing data from your system.
How does this happen?
- Multiple security failures
- Needs a human factor
- Poor network segmentation: linux > fileshare device > data files
- ***Over privileged users: too many users with (unnecessary) administrative rights***
- Poor outbound filtering
Ransomware
Scott then addressed a more familiar, current form of malware: Ransomware.
Ransomware Operation
Ransomware typically starts off with a user navigating to a website, and clicking on something they shouldn’t have clicked on. The exploit is then downloaded from that website to the user’s computer. At that point, the exploit is inert; not harming anything on the target computer—and can be removed before the software does damage. There are security tools—behavioral-based protection—that can detect encryption in-process and stop that process before the hack is successful. However …
If the exploit goes unnoticed … user interaction, a time-delay process, or some sort of call out to the hacker may then trigger further action for the exploit to download the malicious payload portion of the activity, which is where the software is going to encrypt the data on the user’s system. At that point, there’s not a lot that can be done. Once a form of ransomware has been triggered, there’s typically not a cleanup tool (like Malware Bytes) that can be used to recover.
Cryptowall Ransomware
Cryptowall is a familiar ransomware that encrypts significant files on the computer, based upon file extensions; this software excludes certain extensions. Excluded extensions include all the executables and other useful files. Then a message is displayed, including a message telling you how to buy bitcoins. They’re stringing you along to ensure you have a way to send them money.
Stampado Ransomware
Stampado ransomware has a Mercy Button. The message says, “You probably don’t believe that I have your files and that I’m going to decrypt them. Click the Mercy Button to see an example.” When the Mercy Button is clicked, Stampado decrypts a sample file to demonstrate their superiority. This is an expert form of marketing.
Users: The Biggest Threat
One of the last threats but probably the biggest is: Users. Scott admitted that this is something that even he has been caught up in; his situation had to do with DocuSign, and was a timing issue. Scott related that he was at the bank the day before this happened and, around noon, he received a (legitimate) DocuSign email from the bank. Since this was not at the top of his priority list, he didn’t open it right away. Then, the next day, Scott was working in his email and received another email that appeared to be from his bank; mimicking the previous day’s DocuSign email, roughly 24 hours to the minute. Thinking that this was some sort of a reminder email, he opened the email. So, a timing thing.
Educating Users
IT Security: Which of the following is easier to circumvent?
1. Classic IT Security:
- Backup Tools
- URL Filter
- Password Manager
- Fire Wall
- Encoding
- Trojan Horse | Phishing | Malware
- SPAM Defense
-or-
2. Two guys who may have had an after-work beer…
Compare the above two options as challenges for hackers. No contest. That’s why phishing is such a big deal. Phishing and social engineering via phishing. We must really spend time with users. We can spend dollars with these security tools or we can spend time with users and educate them to the ways in which hackers operate.
Social Engineering
How does social engineering work?
- Curiosity: When we click on certain emails, we’re curious.
- Habit: We’re conditioned to click on buttons.
- Urgency: There’s always a sense of urgency; e.g., this decryption key won’t work in 3-5 days.
- Trust Factor: Depending on who sent the email, if a friend’s email got hacked, and then he sent out a bunch of emails, you might open that email.
That said, how do we protect ourselves?
Technical Prevention
Scott then breezed-through a bunch of technical ways we all can use to prevent hack attacks on our systems.
- Security Awareness Training: This is the most powerful mechanism for technical prevention. Making it clear to all users what is happening and how they might inadvertently assist hackers—and keeping that information top of mind, regularly.
- Check the domain name by hovering over the link to actually see where the link will resolve, compared to what the “link title” says.
- Managed simulated phishing campaigns: testing users to see who needs training; celebrate success of the campaign or discipline those who fell for the scam.
- On-demand phishing assessments.
- Personalized training for end-users caught in a simulated attack.
- Automated reporting on phishing and training results.
EndPoint Security & Ransomware Protection
Some people think of EndPoint Security as anti-virus protection, which is really the concept of what protected us yesterday—or, last year—but may not be what can protect us going forward, today or this year.
Anti-Virus Protection
Typical anti-virus protection protects you against XYZ Strain of virus. The problem is, with the guys creating this type of virus—they’re the smartest guys on earth—the anti-virus software is typically behind the curve, protecting against previous forms of viruses. These days, EndPoint Protection is more behavioral-driven.
Behavioral-Driven EndPoint Protection
EndPoint Protection has changed to behavioral-driven, meaning that this protection is not simply looking for strands of XYZ Virus, it’s looking for the behavior. This protection is looking for something that’s encrypting files on a machine that shouldn’t be encrypted. For example, if the user is seeing that their fileshare files starting to be encrypted, EndPoint Protection is smart enough to promptly stop that behavior rather than simply stopping that strain of virus, and then put those files back in place. So a whole different level of security is catching up to being more behavioral-based rather than signature-based.
Encryption
The biggest part of encryption Scott hears especially with our healthcare clients (HIPAA Clients) is: “We don’t keep PHI on our tablets.” But Scott is of the opinion that if he looked at them, there would be some Protected Health Information on those tablets. For example, take anybody’s laptop … you might have a password on that laptop but if somebody gains access to your device and they pull out the hard drive, and if that hard drive is not encrypted, they will be able to get whatever information off that device they want to get. So encrypting devices is becoming more and more important, and is one of the areas where the cost of remediation today, with Windows 10 specifically, has dropped considerably, to where encrypting Windows 10 devices costs are low compared to the cost of a big risk mitigation. So encrypting Windows devices is something that should be considered.
Mobile Device Management
As more and more people are using mobile devices (iPads, Android Phones), more and more information is on those devices, and we must consider how we manage those mobile devices, how we encrypt those devices.
- Containerization
- Web Security
- App Black List
- Configuration
Firewall Management
Firewall used to be simply the equivalent of a virtual brick wall between the Internet & the network. Now that firewall software can do so many more things like scan for viruses, scan for ransomware, scan for email protection, scan for files leaving your network; not simply inbound things, but scan for data loss to notify you if you got one of those malware strands, and if that software is sending outbound information from the fileshare, the firewall can actually promptly stop that process.
How do we manage the following smart firewall technologies?
- Next Generation Protection
- Sand-boxing, Web app control, AntiVirus
- Synchronized Security
Ask yourself the following question: Are we using a firewall that employs Next Generation Protection Technologies?
Synchronized Security
The whole concept of these technologies is that each of these example prevention technologies—and that’s not all of them—is a Point Solution; a point where your device is going to be encrypted, and that’s going to take care of one specific problem. Then there’s another Point Solution which is your Firewall. And there’s another Point Solution which is the EndPoint Security.
The goal today is to synchronize all of our security procedures into one package; to have a security strategy, compared to employing different pieces of technology to stop different individual threats—and maybe they don’t even talk together—so there could be holes in that strategy.
The point is: going out and buying an anti-virus solution and firewall and encryption software is going to be better than not having anything but that action is not going to be as good as developing a full strategy which starts with looking at the organization as a whole and then determining, “How do I go about this?”
Scott suggests starting at a higher level and determining how you’d develop a strategy for the company as a whole and determining where your biggest risks are and then figuring out how you can synchronize all the pieces.>Security Guarantee
Wrapping up, Scott admonished his audience, “With those things, we can almost guarantee we’re secure. Right? Nope. Not a chance.”
Handoff
To manage that desire for guarantees, Scott explained that Tom’s talk focuses on data breaches. Because one thing we’ve heard from clients over the years is, “Hey, we’ve got you guys for that.” Scott’s reply? “While we’ve got a lot of smart guys on our team, there are many others out there whose main purpose in life is to break through all the security prevention we put in place, or the security strategies we put in place. And, at the end of the day, we all still have people working in our company. And, if I’m clicking on a DocuSign Email, and I was training on that very point the previous day and I’m still clicking, we’re definitely going to have people who aren’t as aware. Keep that awareness top of mind.”

Risk Mitigation
Scott turned the presentation back to Tom to talk about Risk Mitigation, the next step. Tom began by stating, “If you think that what Scott shared is important, consider this: any piece of information that you touch becomes your responsibility. If you become a conduit for that information landing in the hands of the desperados, guess what: the law will tell you that you are responsible to do three things:
- You have to hire a forensic company to come in and discover the source of the hack, and did the hack start with you?
- If the hack did start with you, then you’re required to notify all of the people that you have breached.
- Then you’re required to provide monitoring to the people affected.”
State Data Laws
There are only two states in the Union that do not have data laws: Alabama and South Dakota. If your company has a breach of over 250 consumers, then you have to report that to the State, and they want to see what the notification you sent out looks like.
Every member of the audience will be able to find some company in their industry on the Oregon Department of Justice website’s Data Breaches Page; nicknamed the Wall of Shame.
[Author’s Note: most common categories listed on this website are hotels, restaurants, retail stores, grocery stores, coffee shops, realtors (for those of you who buy your house with a credit card…), drug stores, universities and school districts, health care providers and labs, investment firms, and cellular service providers.]
Tom explained, “We’re told that each notification that goes out costs about $200 a head. So if you are the conduit for a major breach and you are a small business, they say half of you are done; you would not be able to afford the cost of going through the mitigation process. Every time you run a credit card, every time you have a batch of information that’s available, as Scott pointed out very well, the issue is not just that you have that, and they want that information, but if you are the conduit for that information getting hacked, then you are responsible.”
Scott: “And, the scary part is: the consideration is not just the cost of notifying all of your consumers … to me, it’s the P.R. And, especially in health care, what we’ve seen in the past year is that HIPAA breaches used to be that thing that was talked about, and now, the fines that are coming down for ending up on this list are is simply debilitating.”
The Law of Large Numbers
Tom pointed out that Jacob Bernoulli, a 17th century Swiss mathematician first proved the Law of Large Numbers.
Examples of The Law of Large Numbers
If we flip a coin 4 times, maybe one of those 4 times, the coin will come up heads. But, if we flip the coin 10,000 times, we know now that the odds are better, due to repetition. If we get a big enough sample of anything, it’s going to repeat itself. Heads will come up almost 50% of the time.
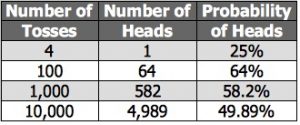
Replica of Probability Slide from Hart Presentation
The Law of Large Numbers is probably most familiar to parents of teenagers who drive the family car for the first time and are shocked when their insurance agent sends them a bill that is outrageous!!! Why? Because we all know that any 16 year-old who is texting or eating fast food while driving the car is going to get in more accidents than a 51 year-old who is boring and only listening to the radio—and watching the road—when they drive.
Transferring Risk
A huge amount of available statistical information is used in the insurance industry to deliver a product that allows us to transfer risk; the idea that we can level-out society. Statistical application to the insurance industry started as a bunch of mathematicians playing dice games, and is the same concept employed by card counters in Las Vegas. They aggregate huge amounts of data and determine that they can offer you a product that will absorb risk in trade for a premium.
Cyber Insurance
As you consider the idea of insurance, managing risk, and thinking-through what you’re doing when you buy a policy, consider this: there are guys out there with a huge amount of information and ingenuity and marketing who are offering you the opportunity to transfer risk (something that can destroy your business) for a known amount of money. You’re going to give them a premium every year. And, in trade for that premium, they’re going to give you a promise.
Forensics Specialists
When you have an insurance policy and you discover a breach, you can call your insurance agent and the first thing they do is call a forensics guy to come out—and forensic techs are specialists. These specialists come out and figure out where the breach happened. They’re already set up with all 50 states to send out the notifications and then they set up monitoring. Again, you could do all that yourself or you can choose to transfer that risk to somebody whose primary job is to simply handle the situation.
We have this tremendous opportunity, particularly in America and the West, to allow the market forces of insurance to level that which can destroy our business. And, right now, in the information world, these intrusions are the new threat. We all insure our buildings. We all insure our cars. We’re all worried about many other threats to our businesses, but we have to consider information as a threat to business continuity.
Assessing Probabilities
When we talk about insurance, we can ask, “Well, what’s the probability that event is going to happen?” But for those things that are probably going to happen, we’re going to have to do something. We either have to know—and accept—the risk or we have to do something else. We have to realize that we’re going to have to transfer that risk to somebody else. So, if you want to play in the same arena as these guys, who are basically in the same group as the guys in Vegas who set the line, who say, “OK. On Sunday, we all know the Patriots are going to win and they’re going to win by 5.5 points so you are more than welcome to place your bet and take the points or you can pick the other line” … if you want to be able to access this risky world of the Vegas Guys, who are absolute professionals at setting the line, at taking on this risk, all you have to do is go to Bob The Bookie. This is the guy who sits in Vegas and takes the line on your bets.

Bob The Bookie; replica from Hart Insurance Presentation
These days, we would say, “be careful”, “be aware”, and make sure that part of your insurance program includes talking to somebody about information; not only what you are doing with that information but how you’re going to handle an attack, if and when something happens.
The desperados—those who are out there attacking us and our computers—are going to be there. How are we going to manage that? And the best way to manage that risk is in tandem: not only deal with the physical part, but also the risk management portion of what you’re going to do if and when a breach happens.
Risk Managers
Scott: “And, really, as Tom said, the risk management is the issue, and we feel our job is to present you and our clients with the risks that are out there. On the same level, you are welcome to accept some risks. Right? We can’t plug every hole. And, there are certain risks that we know we have to address as best we can. And there are others about which we say, ‘I’m OK with accepting that risk.’ So have that discussion and keep the idea top of mind.”
There’s no job position that is invulnerable … from the bottom of the ladder to the top. Nobody is immune from attack.
In Closing
Key things to remember when dealing with email:
- Normalcy: Is it something out of the norm?
- Urgency: There’s always some sense of urgency … you must act by a specific time. Some sort of a call to action.
Send suspicious emails to IT Department so they can put it in a sand-box and check it out.
Safe Links Protection for Outlook.
** Be sure to hover over “labeled” links to see where the link will resolve … and be sure the domain is not: You’reScrewed.com
Also: check the address of the sender if you are concerned about a “friend” who has emailed you.
Summary
The goal of this CyberSecurity Seminar was to explain how attacks happen and identify sources of problems and enlighten business owners regarding the need to educate their users. Goal Accomplished!
For more information, you are invited to visit Scott’s and Tom’s websites:
CORE Business Services Website
***ADDENDUM*** (updated 3/10/18)
The following commentary is provided by a freelance CyberSecurity Consultant, and serves to buttress the excellent CyberSecurity Seminar information.
[Author’s Note: History has demonstrated that we all must be very careful with email. The following examples of previous cyber attacks—or, exploits—provide warnings about the potential for delivery of destructive payloads. The purpose of recounting these attacks is to educate users as to how an exploit can be presented as innocuous but can in fact be very destructive. As Scott and Tom discussed during their presentation, the bad guys are working around the clock to devise new and clever ways to entice people into falling into traps in order to enrich themselves.]
Clicking on a link, or worse, just viewing an email message—even one sent from somebody you know—can be enough to activate the attack code. Usually this is by exploiting a bug.
Some famous exploits have included the Windows library that renders graphics, so simply viewing a picture in your web browser or email client is enough to compromise your system. Most often this happens when the email is viewed as HTML. This is why many email clients don’t automatically render HTML email; they show just the text part, then make you click a button to view the HTML version.
One known attack took advantage of a bug in the Microsoft DLL that renders images, so a carefully crafted image attachment was used for a while as an attack vector. Same thing for multi-byte character handlers. There was also an attack that took advantage of a bug in the handler for the SMTP header; in that case the attack could happen even if the body of the email was completely empty.
Other attack vectors take advantage of the helper programs automatically started by your web browser and/or email client based on the MIME type of the payload.
This is why one of the recommended security measures is to disable HTML messages in your email client and use text email only. And never open an attachment no matter who sent that email—many viruses spread by taking over a machine and then emailing itself as an attachment (usually disguised as a funny message with pictures, a Word document, etc). So, just because you know and trust somebody, that doesn’t mean opening attachments they send to you is a good idea.
Attack payloads pretty much have to be written to target a specific OS (NOTE: that’s not a comprehensive statement, but covers the majority of them). Windows is by far the most used OS, followed by MacOS, Linux, and ChromeOS, so that’s what the vast majority of attack code is written for. Therefore, those of us who want to have less worry about that sort of thing do most of our public Internet interaction on systems that are too unpopular for virus writers to bother with. OpenBSD is a very good option.
The exploits presented above merely represent the tip of the iceberg, but getting back to the simplistic statement: simply visiting a web page or viewing an email that has attack code can be enough to compromise your system.
The attacks mentioned above have, presumably, been addressed. These specific attacks are not likely to be effective these days. But it’s a game of constant escalation as the attackers keep finding new exploits which the white hats are not yet aware of.
One can’t say that there is currently a known effective attack that can compromise a system simply by reading a plain text email, but one can say that examples have repeatedly been shown that this type of thing is certainly possible.
Patches have been released for the particular examples cited.
Further Reading:
- Motherboard
- CVE (Common Vulnerabilities and Exposures)
- CVE Details; Thunderbird
- CVE Details: Microsoft Outlook
***END ADDENDUM***
ADDITIONAL LINKS:
What could go wrong with this: Amason is taking photos of your front door to show when packages have been delivered.
And then, there’s this recent article on LogicWorks.com: Government Cloud On The Rise: NSA, DOJ Move To Amazon Web Services … and, further AWS information: Cloud Computing for Defense.
Written By: Karen
Vetted By: Scott & Tom
Written: 2/28/18
Published: 3/2/18
Copyright © 2018, FPP, LLC. All rights reserved.